Drop a Specific IP Address and Port with iptables Firewall on Linux Systems

In this article, I’ll show you how to drop a specific IP address and port on Linux systems (RPM Family “Redhat / CentOS / Scientific Linux releases 7 / 6 / 5” and Debian Family “Debian releases 8 /7 /6 and Fedora and Ubuntu). This article will help you to enhance the security of your secured Linux box by blocking a certain IP address from accessing a certain service or all services running on your Linux box. We will stop a ssh brute force attack as an example through this article.
Here’s the security thread which forced me to write this article. I was checking the failed login attempts to one of my secured Linux boxes with this command “lastb” and I found a numerous failed attempts to login to my server with many users account of system or standard services. Of course, my server is under a ssh brute force attack.
To check the failed login attempts to your Linux box ” ssh brute force attack”, run the following command:
# lastb
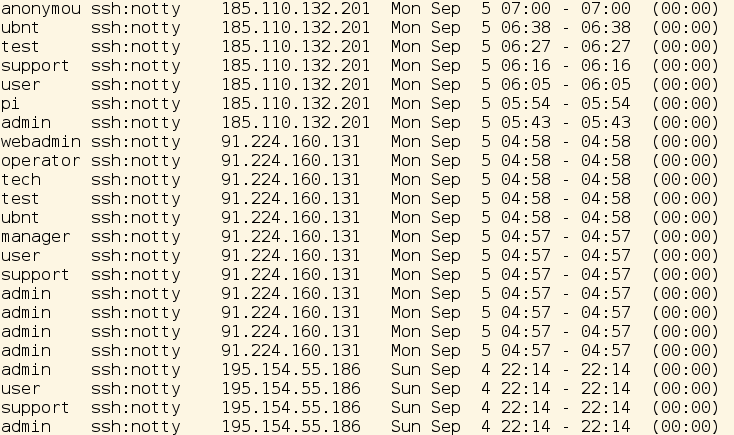 As you see, there are many attempts to login to my production server with different users from different IP addresses. I only display some of the failed login attempts.
As you see, there are many attempts to login to my production server with different users from different IP addresses. I only display some of the failed login attempts.
Of course you and I enabled and run iptables on our production servers. If you didn’t check our previous articles on securing your box with iptables. You can find these articles in our Security Category.
Now, We will drop all traffic to our Linux server coming from those IP addresses. We have two methods to drop those IP addresses:
- Method 1: Drop all traffic from those IP addresses to all services running on my Linux server.
With this method, we will block all traffic from those IP addresses to our server. We will insert our iptables rules to be applied first before any existing rules.
To drop / block IP addresses using iptables use the following syntax:
iptables -I INPUT -s {IP-HERE} -j DROP
So, I will drop all traffic from these IP addresses “185.110.132.201, 91.224.160.131, and 195.154.55.186” by running the following iptables rules:
# iptables -I INPUT -s 185.110.132.201 -j DROP # iptables -I INPUT -s 91.224.160.131 -j DROP # iptables -I INPUT -s 195.154.55.186 -j DROP
We are using two options “-I” for inserting in the INPUT chain, and “-s” for the source IP address we want to block.
- Method 2: Drop all traffic from those IP addresses to a certain service running on my Linux server.
With this method, we will block all traffic from those IP addresses to a certain service running on our server by specifying the service port in our iptables rules. We will insert our iptables rules to be applied first before any existing rules.
To drop / block IP addresses with certain destination port using iptables use the following syntax:
iptables -I INPUT -s {IP-HERE} -p {PROTOCOL-TYPE-HERE} --dport {PORT-NUMBER-HERE} -j DROP
So, I will drop all traffic from these IP addresses “185.110.132.201, 91.224.160.131, and 195.154.55.186” from accessing my SSH server running on my Linux server by running the following iptables rules:
# iptables -I INPUT -s 185.110.132.201 -p tcp --dport 22 -j DROP # iptables -I INPUT -s 91.224.160.131 -p tcp --dport 22 -j DROP # iptables -I INPUT -s 195.154.55.186 -p tcp --dport 22 -j DROP
We are using three options “-I” for inserting in the INPUT chain, “-s” for the source IP address we want to block, “-p” for specifying the protocol type the service work on, and “‐‐dport” for the service port we want to prevent /block access to it from those IP addresses.
So, Here’s come an important question, When Do I use Either Method 1 OR Method 2?
It depends on the type of the services your Linux server provides.
If your server provides a public accessible services such as http, dns, mails, etc…. then you should use method 2. This will prevent the brute force attack “ssh attack in our case”, and also not dropping all traffic from those IP addresses i.e there may be another users using the same IP addresses trying to connect to your http server or dns server running on your server “a normal users”.
But you can use method 1, if those IP addresses are trying to attack different services running on your Linux server, in this case you Must use method 1 to drop all traffic from those IP addresses.
Using either method 1 or method 2 to drop the IP addresses depends only on what services are running on your Linux box and to whom.
Now, after we have applied method 2 to block the IP addresses with ports, let’s check on the applied iptables rules, run the following command:
# iptables -L -n --line-numbers
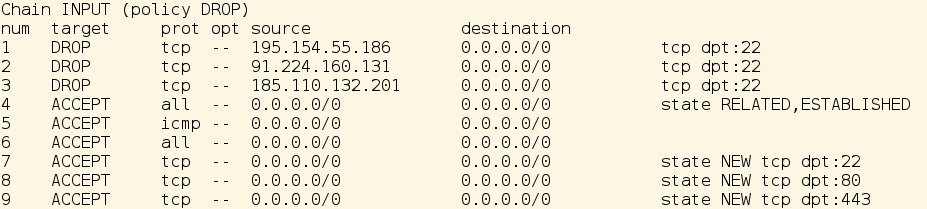 As you see from the above output, the last applied rule has the number 1 “the first rule iptable will check IP addresses against”. Remember that we use iptables rules with option “-I” which caused the applied rules to has the lowest numbers.
As you see from the above output, the last applied rule has the number 1 “the first rule iptable will check IP addresses against”. Remember that we use iptables rules with option “-I” which caused the applied rules to has the lowest numbers.
At this point, we successfully blocked IP addresses and ports using iptables, and stopped a ssh brute force attack to our server. But before ending this post there are some extra info you may need when dealing with blocking IP addresses, we shortly list them as follow:
- To Block a subnet of IP addresses (mo.yy.se.ww/ss).
Use the following syntax to block all traffic from this subnet 10.0.0.0/24 :
# iptables -I INPUT -s 10.0.0.0/24 -j DROP
- To View Blocked IP Addresses with it’s iptables rule numbers.
Simply use the following command:
# iptables -L -n --line-numbers
- To Delete Blocked IP Addresses from the applied rules.
All you need is the rule number of the blocked IP address ” the output of the previous command”, then use the following iptables command to delete the applied rules “number 1” and allow the IP address to get access again to your server:
# iptables -D INPUT 1
Now, the IP address “195.154.55.186” can try to login again to our Linux server.
Hints: 1. All the applied iptables rules in this post is non-persistent, it will be gone with the next reboot or iptables service restart. 2. To make it persistent, you should read our previous posts in our Security Category.
Summary
In this article, we have explained two methods for using iptables command to block / drop IP addresses from accessing your Linux server “all services” and blocked them from accessing certain service ” block access to a certain ports on your Linux box”. We showed you how to list the applied iptables rules, how to add and delete iptables rules with certain IP addresses. We worked on blocking access to ssh server “simply blocking and stopping the ssh brute force attack”. All our rules applied using iptables cli, so you need to save your applied rules to be persistent.
I hope this article is good enough for you.
See you in other articles.

If You Appreciate What We Do Here On Mimastech, You Should Consider:
- Stay Connected to: Facebook | Twitter | Google+
- Support us via PayPal Donation
- Subscribe to our email newsletters.
- Tell other sysadmins / friends about Us - Share and Like our posts and services
We are thankful for your never ending support.